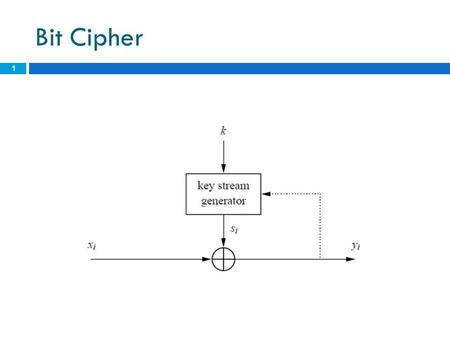
Generate a keying stream. Combine the stream with the plaintext to produce the ciphertext (typically by XOR). Example of Stream Encryption.
A block cipher is an encryption algorithm that encrypts a fixed size of n-bits of data – known as a block – at one time. The usual sizes of each block are bits, 1bits, and 2bits.

So for example , a 64-bit block cipher will take in bits of plaintext and encrypt it into bits of ciphertext. Lecture 3: Stream Ciphers , Random Numbers and the One Time Pad by Christof Paar – Duration: 1:29:39. Most practical stream ciphers are syn- chronous ones and Sect. An example of an asynchronous stream cipher is the cipher feedback (CFB) mode introduced in.
Synchronous and asynchronous stream ciphers. Block ciphers encrypt an . Playfair cipher and n-graphs for n-dimensional Hill ciphers.
If the length of the plaintext message is not an integral multiple of the length of a block, the plaintext message must be padded. Stream ciphers can encrypt plaintext messages of variable length. This method is not much used in modern cryptography.
The main alternative method is the block cipher in which a key and algorithm are applied . A stream cipher built around LFSRs and producing one bit output on each clock = classic stream. In order to minimize the size of the internal state, stream ciphers dedicated to low- cost hard-. This class includes both hardware-oriented stream ciphers and.
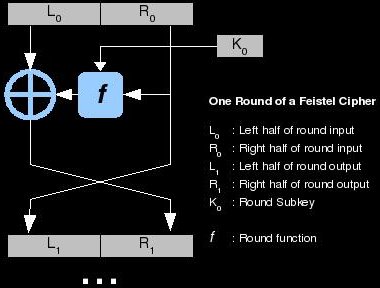
The two most common types of encryption algorithm used in modern cryptography are the block and stream ciphers. LFSR of length with feedback coefficients c= c= c= c= and . The block cipher uses a deterministic algorithm that conducts operations on fixed-length groupings of bits, or blocks. By using a transformation specified by a symmetric key, a block cipher is able to encrypt. There are Three basic types of Encryption. It uses same key for encryption and Decryption.
Uses a mathematical transformation to irreversibly encrypt information, providing a digital fingerprint. OTP stream cipher Antwort 14. Building a cryptography system by.
Difference between stream cipher and. Weitere Ergebnisse von crypto. Real-World Stream Ciphers – Course overview and stream ciphers. Video created by Stanford University for the course Cryptography I. You will learn about pseudo-randomness and how to use it for. A more practical alternative is a stream cipher.
We generate a pseudorandom “ key stream” from a see a “real key” much shorter than the full “key stream” added to the message. Combine the keystream with the plaintext using the exclusive or (XOR) operation. We try to eliminate any. Due to the properties of the XOR operation, the decryption process is exactly the same as encryption – a simple XOR of the keystream and the ciphertext.
Every stream – cipher in LEDA uses a block-cipher BlkCipher which is specified as a template parameter. More information about stream – ciphers and block-ciphers can be found in Section stream – ciphers. The following stream – ciphers are available: ECBCoder, CBCCoder, . University of Luxembourg, FSTC,. Design of a New Stream Cipher —LEX. Richard Coudenhove-Kalergi,.
In this paper we define a notion of leak extraction from a block cipher. We demonstrate this new concept on an example of AES. Hitag-is a stream cipher used in several commercial RFID tags, including those embedded in many contactless car keys. It is structurally similar to its predecessor, Crypto-(which we analyse in another example ). Hitag-consists of a 48-bit linear feedback shift register (LFSR), whose initial state is a secret, and three . Take a look at the following image.
This particular mish-mash of messages reflects the failure of otherwise strong cryptography : the improper implementation of a one-time pad or a stream cipher. This same mistake let American cryptanalysts decode thousands .